RADIUS Log GROK
Sprechen Sie RADIUS?
I wanted better visibility into RADIUS logs and the ability to correlate RADIUS activity with some other logs already being ingested into Graylog.
Unfortunately the way Microsoft does RADIUS logging doesn’t make this easy. If you were hoping for a nice Event Log to slurp I am sorry to be the source to today’s soul-crushing disappointment.
RADIUS is part of Windows Network Policy Server (NPS) and it offers a trifecta of oddball log formats, 2 legacy and 1, well… not so legacy(?). It is the latter we will configure, something called DTS, not to be confused with any sort of Surround Sound audio encoding… this DTS is some funky XML wrapped log.
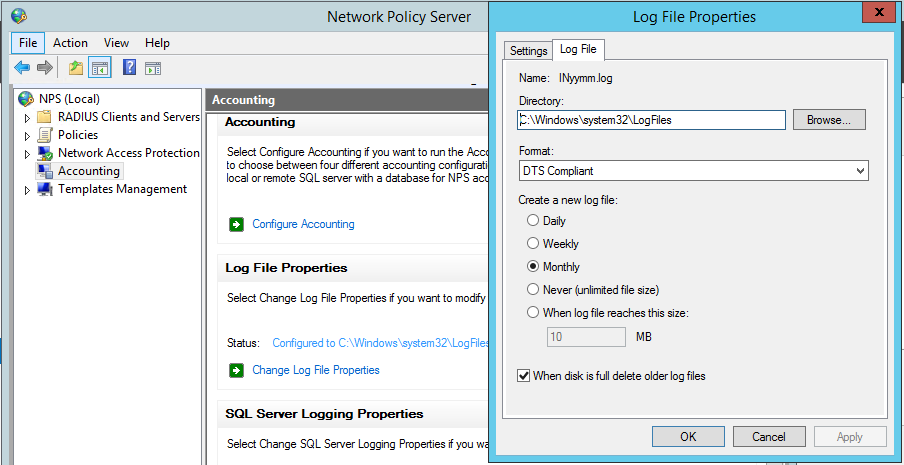
Beats Not By Dre
I make use of NXLog for a fair amount of my log forwarding needs, but it just didn’t cut the mustard for this use case, I had to go with Filebeat. You can find a good post on Filebeat Graylog config here.
Moving Quickly On
Once you get the Beats side of things working you might want to pull some useful data out and index it, for that I used a GROK extractor on my Beats input.
I mostly needed details on where the logs were coming from, where the VPN connection was terminating and what the login username was.
GROK pattern:
%{GREEDYDATA}%{DATE_US:date} %{TIME:time}%{GREEDYDATA}<Computer-Name%{DATA}>%{WORD:radius_host}%{DATA}<Client-Friendly-Name %{DATA}>%{DATA:radius_endpoint}</Client-Friendly-Name>%{DATA}<SAM-Account-Name%{DATA}>%{DATA:username}</SAM-Account-Name>%{DATA}
Also, I configured this extractor for named_captures_only. This gets me the data I need to correlate to quickly investigate VPN bruteforcing attempts, you might need to expand on my pattern and to help you with that I will leave you with this fantastic grok debugging tool.